Understanding the Different Types of Keys in DBMS in 2025
Confused about primary, foreign, or composite keys? Learn the 7 types of keys in DBMS and why they matter for building scalable, secure, and efficient web apps.

In the world of database systems, keys are not just technical terms thrown around by developers; they're the backbone of relational data structures. Whether you're building an e-commerce platform, a customer management system, or even a booking app, understanding the types of keys in DBMS is critical for making your app reliable, scalable, and user-friendly.
In this blog, we break down the different types of keys in DBMS in a way that’s friendly, visual, and designed to help non-tech founders, entrepreneurs, and business teams understand the mechanics behind the systems they depend on.
What is DBMS?
A Database Management System (DBMS) is a software system designed to manage, store, retrieve, and manipulate data in databases. Think of it as a smart organizer that allows users and applications to interact with data efficiently and securely. It provides tools for defining, constructing, and controlling access to the database, making sure the right data gets to the right people at the right time.
There are several types of DBMS, relational (like MySQL, PostgreSQL), document-based (like MongoDB), key-value stores, and more. Among them, the Relational DBMS (RDBMS) is the most widely used, especially in enterprise systems, because of its structured approach to organizing data in rows and columns.
One of the most important concepts in RDBMS is the use of keyS, which help uniquely identify records and establish relationships between different tables. This brings us to the focus of this blog: understanding the types of keys in DBMS.
Why Should You Care About Keys in a Database?
Let’s say you run a fitness app. If you have 2 users with the same email ID or booking ID, your entire system might break down. Ever wondered why some apps don’t let you change your email address or why a single product entry is linked across reviews, orders, and inventory? It all comes down to keys.
In databases, keys are used to uniquely identify rows, connect tables, and enforce data integrity.
Knowing what are the different types of keys in DBMS helps you understand how your system behaves and why your developers make certain architecture decisions.
The Core Concept: What Are Keys in DBMS?
In DBMS (Database Management System), a key is a field (also known as an attribute) or a combination of fields used to identify a specific record (row) in a table uniquely. Keys ensure that there is no ambiguity or duplication of records, which is crucial for data accuracy and consistency.
Imagine a student database. If multiple students have the same name, how can we differentiate them? A unique identifier, like a Student ID, serves as a key. This identifier guarantees that each student can be individually recognized regardless of whether they share names, birthdates, or other common attributes.
Keys also play a critical role in linking tables. For example, a foreign key in one table might refer to a primary key in another table, allowing the database to establish meaningful relationships between related data sets, like connecting students to their enrolled courses.
In essence, keys help to:
- Maintain Uniqueness: Prevent duplicate rows in a table.
- Ensure Data Integrity: Avoid incorrect or conflicting data entries.
- Enable Relationships: Connect data across multiple tables.
- Improve Performance: Serve as indexes to make searches faster.
Without keys, managing large volumes of structured data would become chaotic and unreliable.
How Many Types of Keys Are There in DBMS?
There are 7 essential types of keys in DBMS that you should know:
Let’s Breakdown of Each Type of Key in DBMS
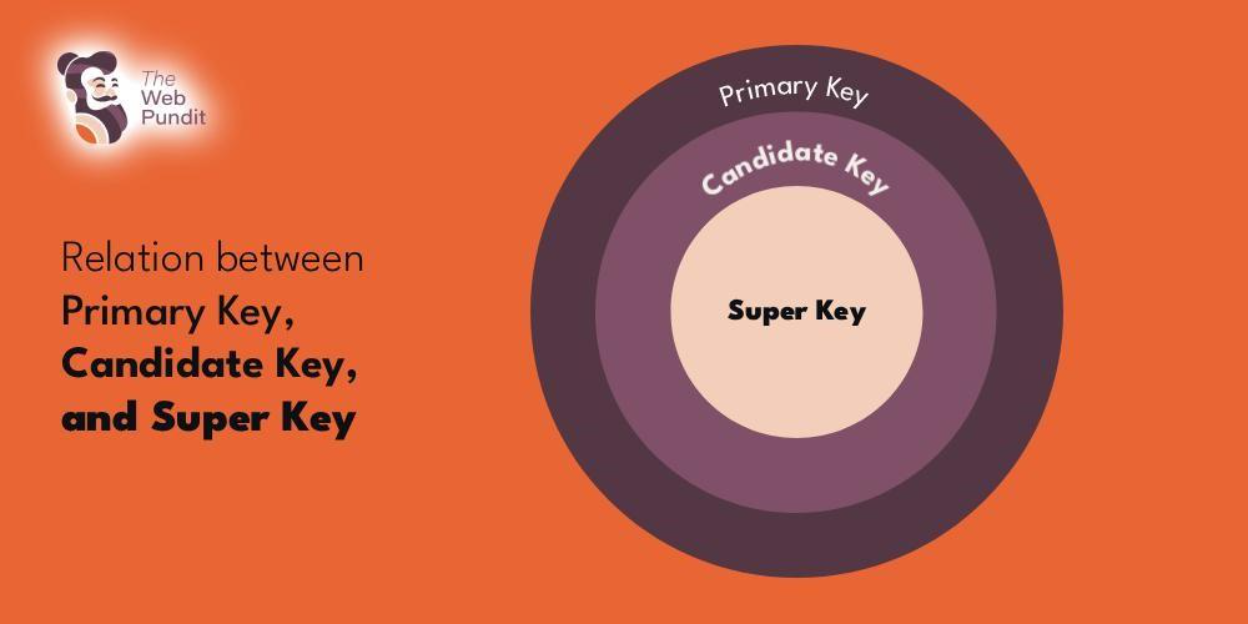
1. Primary Key
A primary key is a special column (or set of columns) in a table that uniquely identifies every record. No two rows can have the same primary key value, and it can never be left blank.
Example:
In a Students table, the Student_ID can be the primary key because every student will have a unique ID.
Here, Student_ID is the primary key.
2. Candidate Key
A candidate key is any column (or group of columns) that can uniquely identify a row in a table. There can be multiple candidate keys, but only one is chosen as the primary key.
Example:
In the same Students table, both Student_ID and Email could be candidate keys. Both are unique, but we choose one (like Student_ID) as the primary key.
3. Alternate Key
Once you've chosen a candidate key to be the primary key, the others become alternate keys. They're still unique and useful, just not the main key.
Example:
If you choose Student_ID as your primary key, then Email becomes an alternate key.
4. Foreign Key
A foreign key is a column in one table that links to the primary key in another. It helps maintain relationships between tables.
Example:
Let’s say there’s a Courses table, and each course record includes a Student_ID to show which student is taking that course.
Here, Student_ID in Courses is a foreign key referring back to the Students table.
5. Composite Key
A composite key is made up of two or more columns used together to uniquely identify a row.
Example:
In a Student_Courses table that tracks which student takes which course:
Here, neither Student_ID nor Course_ID alone is unique. But together, they form a composite key.
6. Unique Key
A unique key ensures that all values in a column are different, just like a primary key. However, a unique key can contain null values, whereas a primary key cannot.
Example:
In a Users table, Phone_Number can be a unique key. Every user must have a different number, but it can be blank for users who haven't added a phone number yet.
7. Super Key
A super key is any combination of columns that can uniquely identify a row. It includes all candidate keys and more.
Example:
In the Students table, both Student_ID, and the combination of Student_ID + Email are super keys, because they can uniquely identify records.
Overview of Different Types of Keys in DBMS
So, Why Should You Care?
To summarize, the seven types of keys in a DBMS -Primary Key, Candidate Key, Alternate Key, Foreign Key, Composite Key, Unique Key, and Super Key, are not just textbook concepts. They’re the backbone of how data is stored, connected, and accessed in any application.
Understanding these helps you make smarter choices when planning your app’s backend architecture.
Why does this matter to you?
Because poor key management leads to:
- Duplicate or lost data
- Broken relationships between data tables
- Difficulty scaling your app
- Inefficient queries that slow down performance
If your app handles user data, transactions, products, content, or anything relational, knowing how these keys work could save you hours of debugging, rework, and future tech debt.
So, the next time your developer says, "We need a composite key for this use case" or "Let’s make phone number a unique key," you’ll understand that it’s not just coding jargon, it’s a smart move for long-term scalability and data health.
At Web Pundit, we don’t just build web apps — we design scalable, robust, and intelligent systems. Understanding how keys work in DBMS helps us avoid costly database refactors down the road and ensures your product is engineered for scale from day one. In fact, we’ve even covered the most powerful technologies that power this scalability — check out our Definitive Guide on Top Backend Frameworks for Web Development in 2025 to explore what’s shaping backend architecture today.
Final Thoughts: Build Smarter Apps with The Web Pundit
At The Web Pundit, we don’t just write code — we engineer systems that are built to last.
Whether you're building a new SaaS platform, a custom CRM, or even a simple internal tool, your database schema is the foundation of your product. And the way you use keys in DBMS plays a major role in that foundation.
Most performance issues, data duplication problems, or user identity conflicts can be traced back to poorly structured data and missing key constraints. That's why our team takes schema design seriously, using best practices to build smart, future-proof databases from day one.
If you're planning:
- A new web or mobile app
- A backend revamp or data migration
- Or need help cleaning up a legacy database system
We’re here to help. With a strong focus on scalability, integrity, and performance, Web Pundit ensures that your data architecture aligns with your business goals.
Ready to get your data foundations right?
Let’s start with a free consultation. Contact The Web Pundit today and discover how intelligent DBMS design can transform your application’s stability, performance, and growth.




